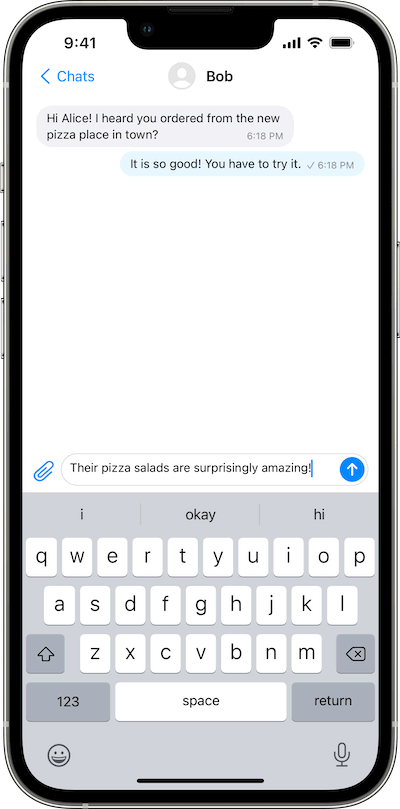
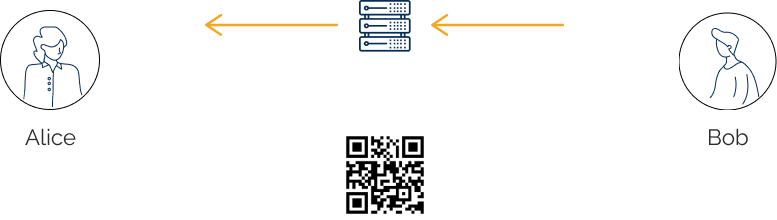
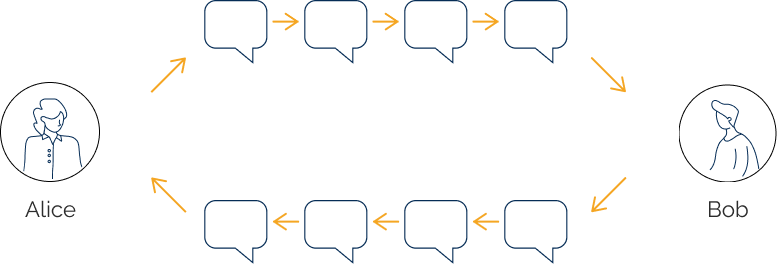
Use SimpleX
SimpleX chat terminal client
v2.0.0 is
released!
– groups and files
– two-layer E2E encryption, with double-ratchet algorithm
– protocol is compatible with mobile apps
You can use our servers or deploy your own, e.g. using StackScript on Linode.
Sign up to be updated about the new releases.